Minneapolis and Rochester public schools suffer severe data breaches
May 2, 2023
Minneapolis (MPS) and Rochester (RPS) public schools have been victims of ransomware attacks. Both districts recommend anyone possibly affected change their passwords on any account accessed through their networks. They also say to stay alert for suspicious emails and phone calls.
What happened?
MPS suffered an attack by the Medusa ransomware group. MPS first put out a statement about the attack on February 21st. They encrypted MPS’s files and asked for 1 million dollars for the decryption key. MPS did not pay the ransom and after a stated deadline of March 17th, the Medusa group posted the data to their dark web blog. This data goes back to 1995.
It is not known who is responsible for the RPS attack or if any stolen data has been published online.
What is ransomware?
A ransomware attack is when a group of hackers gains access to a network and encrypts (locks) all data. The hackers then demand a ransom (usually paid in Bitcoin) for a decryptor code (a key to unlock the data). This can be very disruptive to an organization. However, if an organization pays the ransom, the hackers will see that they may be willing to pay again. This can lead to repeated ransomware attacks by the same group or different hacker groups.
How can I protect myself?
“There is not a device that isn’t hackable,” said local cybersecurity expert Michael Funk during an interview with local news station KTTC after the Rochester attack. However, there are steps you can take to secure yourself in case of an event like this.
- Make strong passwords – It’s much harder to crack a complex password than a simple one. A password like “password123” would be much easier to guess than “QftP3895$”.
- Don’t reuse passwords – If one website suffers a data breach, any account using those same login credentials can be logged into. Especially don’t reuse passwords for important things such as online banking.
- Keep devices up-to-date – Many software updates come with security updates to patch out vulnerabilities that can be used to hack devices. Stop hitting “remind me later” when it’s time to update. The more you wait, the longer you may be vulnerable.
- Use MFA – Use multi-factor authentication. I recommend using an authenticator app such as Authy, Microsoft Authenticator, or Google Authenticator.
- Create backups of your data – This can be done using a cloud service like Google Drive, iCloud, or OneDrive. These services back up your data to a secure server somewhere in the world. One downside of these services is that you have to pay a monthly or yearly fee to use them. They’ll give you some storage for free but if you want anything substantial, you’ll have to pay. You could instead use a physical drive to back up your data. You’ll only have to pay a one-time fee for the purchase of the drive. The downside is that if the drive gets damaged or lost, your backups are lost.
- Use common sense – Humans have a great sense of danger, listen to it! You are your computer’s first line of defense. If a link feels suspicious or if an offer is too good to be true, stop and click away.
How the ransomware operates
According to cybersecurity and tech news website Bleeping Computer, the Medusa ransomware shuts down 280 Windows processes. These include mail servers, database servers, backup servers, and security software. This makes it difficult to detect the ransomware or to inform others of the attack. Medusa then deletes Shadow Volume Copies. Shadow Volume Copies can be used to restore lost data.
They then download the data to their servers and encrypt the data on the host servers. All files are encrypted to a .MEDUSA file. It’s not uncommon for hacker groups to add their own little flair to their attacks. The user is then presented with a text file (named !!!READ_ME_MEDUSA!!!.txt) saying that their data has been encrypted, instructions to contact them, and a payment deadline. If the ransom has not been paid by the deadline the data is released on Medusa’s blog.
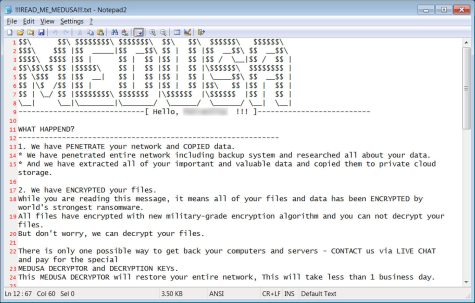
A screenshot of !!!READ_ME_MEDUSA!!!.txt
Source: BleepingComputer
The Medusa ransomware has no known weaknesses as of this time.



